- IOTA launches its decentralized identity framework in alpha, aiming to enhance digital trust.
- The system provides verifiable, self-sovereign identities for finance, IoT, and enterprises.
IOTA has released the alpha version of its decentralized identity framework, aiming to solve trust issues in digital interactions. The system enables individuals, companies, and devices to establish provable identities without relying on central authorities.
Through blockchain and cryptographic security, IOTA Identity provides a high-tech digital verification solution with privacy and agency.
The alpha release of #IOTA Identity is here! A decentralized identity framework for secure digital interactions 🔐
From finance to IoT, trust in digital identity is evolving. Let’s dive in! 🧵👇 #SSI #Blockchain pic.twitter.com/GAUpzpJXug
— IOTA (@iota) March 18, 2025
Today’s online platform is where data is being transmitted across different mediums, but it is hard to keep it authentic. Fraudulence, data manipulation, and security issues have increased as verification channels have not been dependable.
Traditional identity systems rely on central authorities having the power to grant access to data, yet this approach is susceptible to possible breach and abuse.
IOTA Identity solves this issue by offering a decentralized solution, reducing dependence on middlemen and leaving users in sole possession of credentials.
Through this new system, IOTA abides by global guidelines set by the World Wide Web Consortium (W3C), which offers guidelines on managing digital identity.
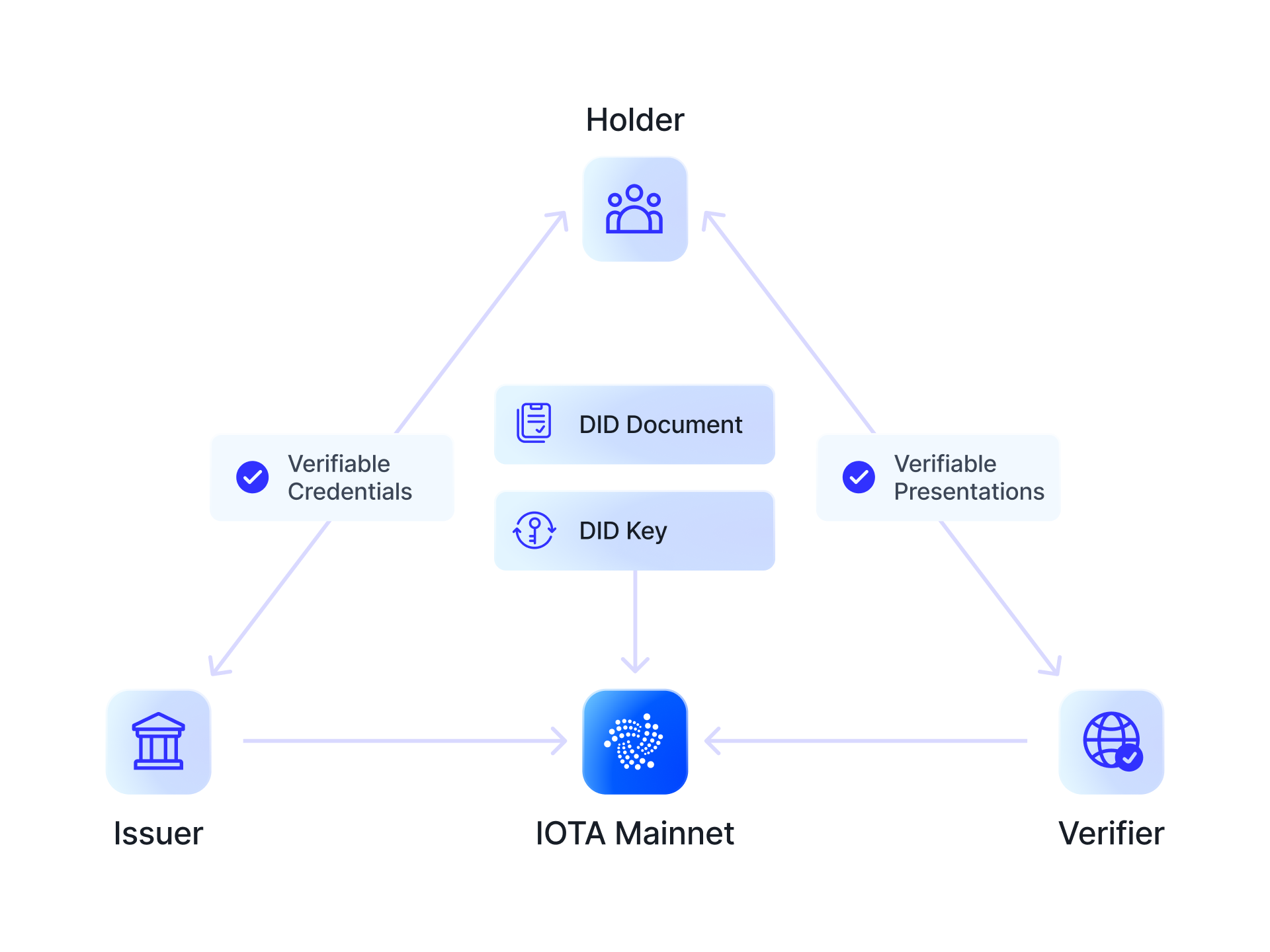
Decentralized Identifiers (DIDs) provide individuals and devices with the ability to own, create, and control identities independently without any third-party interference.
Additionally, blockchain technology ensures that once data is recorded, it remains tamper-proof, offering a secure foundation for authentication across industries.
Expanding Identity Use Cases Across Sectors
IOTA Identity is versatile and is meant to enable secure interaction across different domains. It simplifies Know Your Customer (KYC) compliance, fraud prevention, and digital signatures within the financial sector.
Businesses are able to verify identities without any inconvenience, reducing paperwork and operational costs. It improves compliance with regulations without compromising on user privacy.
Supply chain efficiency is also enhanced through this innovation. Products bear verifiable credentials, so they are authentic and resistant to counterfeiting. Companies have a robust audit trail to trace items across locations.
In the same way, the healthcare industry can leverage IOTA Identity to provide secure patient records, maintaining privacy while granting required access to medical professionals.
The IoT industry stands to gain significantly from this identity system. With billions of devices on the internet worldwide, secure authentication is a necessity. IOTA Identity allows machines to authenticate each other so that secure interaction is possible without involving humans.
From city surveillance to automated transportation and industrial automation, intelligent city systems can function with higher security and efficiency.
For government services, digital identity is increasingly becoming a necessity. IOTA Identity facilitates e-governance, enabling citizens to access services securely without exposing data unnecessarily.
Organizations can integrate decentralized identity solutions into corporate management, employee verification, and fraud-resistant document signing.
How IOTA Identity Protects Privacy with Verifiable Credentials
The IOTA Identity is founded on core digital concepts, including DIDs, verifiable credentials, and decentralized authentication. Unlike traditional identity systems where sensitive data is stored in central databases, IOTA’s approach keeps users in charge.
Identity holders hold credentials, issuers carry out verification, and verifiers check legitimacy without access to the entire data set.
Through the use of verifiable credentials, users can express certain traits without revealing too much. For example, job applicants can validate qualifications without revealing too much personal information.
In the same way, IoT devices also ensure origin authentication without exposing the underlying configuration. This selective disclosure approach offers privacy without compromising security.
Yet, through further integration and advancement, the decentralized system is capable of revamping identity verification across industries so that it is not just secure and efficient, but user-controlled as well.



